What’s on that port?
What’s on that port?
Today, the network admin at $WORK contacted me, saying while running a ZenMap on part of one of the offices, he found several Windows PCs in the AP and Payroll departments that were listening on 80/tcp. This gave him the willies, so he reached out to me to find out WTF. ![]()
Once the IPs of the PCs were converted to names, it was time to investigate.
First, let’s make sure they’re still online and listening as expected:
$PCs = 'PC1','PC2','PC3'
$PCS | Foreach-object {Test-NetConnection -ComputerName $_ -CommonPort HTTP}
(Had to use the Foreach as Test-NetConnection doesn’t allow an array for ComputerName) ![]()
This showed that yes, all three were online, reachable and accepting connections for inbound HTTP traffic. Now let’s see what process is listening on the port:
Invoke-Command -ComputerName $PCs -ScriptBlock {netstat -ano | findstr :80}
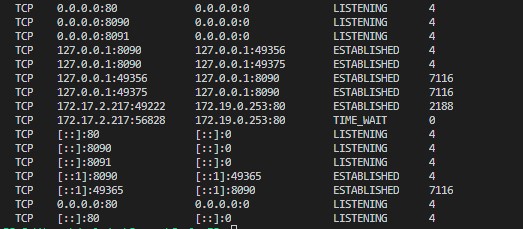
On each computer, the process listening on port 80 had PID 4 (far right column). On a Windows machine, PID 4 is SYSTEM, aka the kernel.
This meant that it wasn’t a user process listening on port 80, so the odds of it being malware or the like went down dramatically. ![]() It also meant that it was almost definitely from the Windows built-in, kernel level HTTP listener (http.sys)
It also meant that it was almost definitely from the Windows built-in, kernel level HTTP listener (http.sys)
Maybe they had something like IIS, MSMQ, etc. installed?
Invoke-Command -ComputerName $pcs -Credential $admin -ScriptBlock {
Get-WindowsOptionalFeature -Online |
Where-Object {($_.FeatureName -like '*web*' -or $_.FeatureName -like '*http*') -and $_.state -eq "Enabled"}
}
Nope, no hits there. ![]()
A bit of Googling for ‘http.sys show http listener’ revealed the handy command netsh http show urlacl, so…
Invoke-Command -ComputerName $pcs -ScriptBlock {netsh http show urlacl | findstr :80}
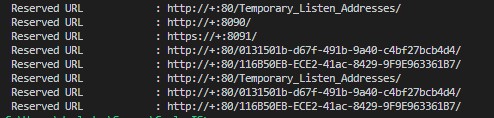
Those look like GUIDs. To the Google!
And one of the first hits was: How can I determine why the System process is listening on port 80?
This indicated BranchCache, which is harmless but maybe undesirable now.

 THWACK
THWACK
Comments